How to design secure SoCs, Part II: Key Management

1. Introduction: The Critical Role of Keys in SoC/ASIC Security
Have you ever wondered how secure critical systems, like medical devices, aerospace systems or autonomous cars, really are when it comes to data protection? One point of the answer lies in effective and robust key management. Cryptographic keys are the digital secrets underpinning device identity, data confidentiality, secure communication, and overall system trustworthiness.
Securing these keys within the hardware environment presents unique challenges, distinct from traditional IT security, due to the intersection of hardware, firmware, and software, exposing them to physical attacks and supply chain vulnerabilities. A robust key management—handling keys throughout their existence—is not just important; it's the fundamental bedrock of chip security.
In our previous post, we provided an overview of secure SoC architecture, highlighting its critical components. This post dives deeper into one of the most critical components: Key management and its aspects within SoC ASICs: the key lifecycle, secure generation and storage, threats, and the role of standards.

---
2. When Keys Come Under Attack: Common Threats
Keys in SoCs face software threats and potent hardware-specific attacks that bypass conventional defenses.
Key physical attacks include:
- Side-Channel Analysis (SCA): Passively exploiting physical leakage (power consumption EM emissions, timing) correlated with secret data. Includes Simple Power Analysis (SPA) and the more powerful Differential Power Analysis (DPA).
- Fault Injection Attacks (FIA): Actively inducing errors (voltage/clock glitching, laser, EMFI) to bypass security checks or corrupt crypto operations to leak keys.
Supply chain risks include hardware Trojans, counterfeiting/cloning, and tampering. Reverse engineering can also expose vulnerabilities. These threats demonstrate that software security alone is insufficient. Hardware-level defenses (RoT, tamper resistance, physical sensors, crypto countermeasures like masking/shuffling) are crucial.
---
3. The Cryptographic Key Lifecycle: A NIST Perspective
The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-57 provides foundational guidance for key management, emphasizing its criticality: "The proper management of cryptographic keys is essential... Poor key management may easily compromise strong algorithms". NIST SP 800-57 outlines comprehensive phases of key management:
- Pre-Operational Phase: Key Generation & Provisioning/Distribution Creating keys using secure methods, approved algorithms, and sufficient randomness and secure distribution of keys
- Operational Phase: Key Storage & Usage & Rotating: Protecting keys "at rest" against unauthorized access or modification, applying keys correctly for their specific, intended cryptographic purpose (encryption or signature, not both) and periodically replacing old keys with new ones.
- Post-Operational Phase: Revocation/Destruction: Securely removing keys from use when compromised or no longer needed, ensuring they cannot be recovered.
- Destroyed Phase: Destruction must ensure keys cannot be recovered or misused.
These stages are interconnected; failure at any point undermines the entire security framework. Generating a strong key is useless if stored insecurely. Effective key management requires a holistic strategy addressing the entire lifecycle.
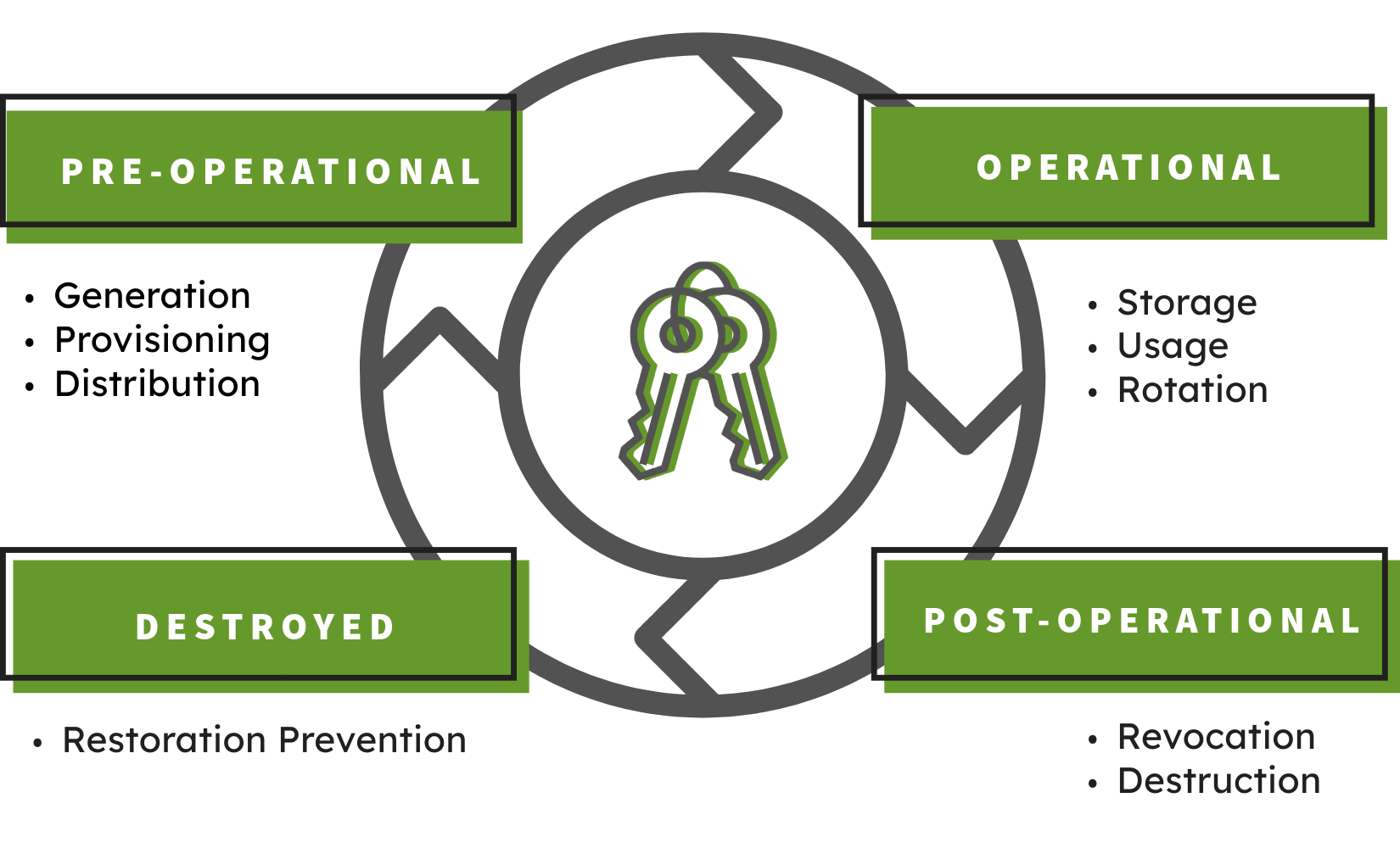
Key-Management-Lifecycle
---
4. Pre-Operational Phase: Key Generation & Distribution/ Provisioning
4.1 Generating Strong Roots: Keys Born Inside the Silicon
Generating cryptographic keys directly within the chip's secure boundaries minimizes exposure compared to injecting external keys. This leverages the hardware's physical properties for randomness (entropy).
Two primary hardware primitives are used:
- True Random Number Generators (TRNGs): Harvest dynamic entropy from unpredictable physical phenomena like thermal noise, shot noise, or clock jitter. TRNGs produce non-deterministic random bits crucial for seeding and cryptographic operations.
- Physically Unclonable Functions (PUFs): Exploit static entropy from uncontrollable microscopic manufacturing variations. These variations create a unique, stable "fingerprint" for each chip, generated via a challenge-response mechanism. PUFs can derive keys on demand, avoiding persistent storage in non-volatile memory (NVM).
PUF effectiveness relies on:
- Uniqueness: Each PUF instance produces a distinct response.
- Reliability (Stability): Consistently reproduces the same response under varying conditions and over time.
- Unpredictability: Computationally infeasible to predict responses.
Achieving PUF reliability despite sensitivity to environmental factors and aging often requires complex error correction (ECC) or helper data schemes, adding overhead and potentially reducing entropy. PUFs also face modeling attacks (potentially using ML) aiming to predict responses. Robust PUF implementation requires careful design, balancing security benefits with costs and risks.
---
4.2 Getting Keys Onboard: The Secure Provisioning Process
Injecting initial keys and configuration data securely during manufacturing is vital, especially with complex, potentially untrusted supply chains. Insecure provisioning risks key theft, cloning, and malware insertion.
Secure methods include:
- Secure Factory Provisioning: Uses dedicated infrastructure linking factory equipment to a central key management service, often leveraging a hardware Root of Trust (RoT) within the SoC as the secure endpoint. Allows secure provisioning at various manufacturing stages.
- Device Self-Provisioning: The SoC generates its unique keys internally upon first power-up, preventing external exposure during manufacturing.
A Hardware Root of Trust (RoT) is essential in either case. The RoT is the immutable security foundation for storing critical keys, secure boot, and crypto operations. Secure provisioning is linked to SoC lifecycle management, transitioning the chip through states (e.g., 'Blank' to 'Provisioned') with increasing security restrictions, like locking key storage and debug access.
---
5. Operational Phase: Key Usage & Storage
5.1 Secure Key Usage within a SoC
Keys are used in many ways in a SoC, e.g. to encrypt and decrypt data that the system processes, to authenticate devices and users, to ensure a secure boot process, to provide digital signatures and much more. It is therefore important to ensure secure use and a number of principles must be observed:
- Clear Definition of Key Roles: Each cryptographic key in a SoC must have a clearly defined role (e.g., encryption, authentication, signing). This prevents keys from being misused or applied to inappropriate functions, which can compromise system security.
- Context-Dependent Usage: Keys should only be used in the contexts for which they were intended. For example, an encryption key should not be used for signing or authentication, ensuring that keys are only used for their specific, designated purpose.
- Access Control: Only authorized components or processes within the SoC should have access to specific keys. Restricting key access prevents unauthorized parties from exploiting the keys and minimizes the attack surface.
- Lifecycle Management: Keys must be managed throughout their entire lifecycle, from creation to use and eventual destruction. Proper rotation and secure storage of keys ensure they remain secure and valid for their intended use.
---
5.2 Secure Storage Strategies in SoCs
Stored keys are high-value targets for software and physical attacks (micro-probing, side-channel analysis, fault injection). Secure storage involves trade-offs between security, cost, flexibility, and performance.
Common strategies include:
- One-Time Programmable (OTP) Memory / eFuses: Non-volatile cells programmed once. Risk: Standard eFuses are vulnerable to physical inspection, and both types are vulnerable if access controls are weak. Basic OTP/eFuse is often insufficient without significant hardening.
- Hardware Security Modules (HSMs): Dedicated, tamper-resistant hardware for secure crypto operations and key management, often adhering to standards like FIPS 140-2.
- Secure Elements (SEs): Tamper-resistant microcontrollers (like smart card chips) excelling at storing secrets and performing specific crypto functions. High physical security, limited flexibility.
- Trusted Execution Environments (TEEs): Hardware-isolated secure processing environments within the main processor (e.g., Arm TrustZone). Allow secure execution of Trusted Applications (TAs), isolated from the main OS. TEEs manage keys and perform complex secure tasks.
Secure storage strategies in SoCs balance security, cost, flexibility, and performance, protecting keys from software and physical attacks. Common approaches include One-Time Programmable (OTP) memory/eFuses, Hardware Security Modules (HSMs), Secure Elements (SEs), and Trusted Execution Environments (TEEs), each with varying levels of security and flexibility. While OTP/eFuses offer basic storage, HSMs, SEs, and TEEs provide more robust protection but with trade-offs in performance and adaptability.
SEs offer a physically distinct, hardened boundary with a smaller attack surface, optimized for storing secrets and simple crypto. TEEs provide greater flexibility for complex software execution using the main processor's power, but have a larger Trusted Computing Base (TCB) and attack surface due to the secure OS, monitor, and TAs, making them potentially more susceptible to software vulnerabilities.
---
6. Post-Operational Phase
The Post-Operational Phase occurs when a key is no longer needed or has expired. This phase focuses on archiving and ultimately destruction of the key. Proper key destruction is critical, as compromised keys pose a potential vulnerability in the system.
- Key Archiving: In security-sensitive applications it may be necessary to archive keys for future recovery. Archiving typically involves secure storage methods, where keys are encrypted and placed in a protected area of the system or external storage.
- Key Recovery: In the event of a system failure or lost key, key recovery mechanisms must be in place. In SoCs, this is often ensured by backup strategies or redundant storage systems that allow for quick recovery of the key without compromising system security.
- Key Destruction: Key destruction is one of the most critical phases in key management. When a key is no longer needed, it must be completely and securely destroyed to ensure it cannot be recovered or misused. This can be done through physical destruction of the storage medium or via software-based methods, where the key is overwritten and the underlying data is rendered unusable.
---
7. Building Trust: Standards and Best Practices
Leveraging standards and best practices is essential for navigating SoC key management complexity.
Key standards include:
- NIST Standards: SP 800-57 (lifecycle, FIPS 140-2/3 (modules), SP 800-53 (controls, incl. SC-12 for key management)
- GlobalPlatform Standards: Standardize SEs, TEEs (APIs, architecture), and Key Management Systems (KMS) for interoperability.
Best practices:
- Centralized Key Management: Simplifies policy, lifecycle operations, and auditing where feasible.
- Secure Lifecycle State Management: Hardware-enforced controls over state transitions (e.g., disabling debug in 'Deployed' state)
- Single Purpose Keys: Using keys for only one function minimizes compromise impact.
While standards provide a foundation, the evolving threat landscape (new SCA/FIA, ML attacks) requires proactive security measures beyond current standards, tailored to specific threat models.
---
8. Conclusion: Elevating SoC Security with Expert Key Management
SoC ASIC key management is fundamental to device security, spanning the entire key lifecycle from secure generation (TRNGs, PUFs) and storage (HSMs, SEs, TEEs) to secure provisioning and defense against physical attacks. It involves complex trade-offs between security, cost, and performance. Achieving robust security demands specialized expertise in hardware security, cryptography, and key management principles. Engaging specialists is often the best path to build secure systems.
At KiviCore, we specialize in providing services that help ASIC/SoC design companies build secure chips from the ground up. Our team of experts works closely with clients to integrate security into every phase of the design and development process, ensuring that chips meet the rigorous security standards required by industries like aerospace, medical devices, and telecommunications.

Our SoC Consulting and Design Services ranges from analysis & check to prototyping and testing.




