ASIC SoC Security
Consulting & Design Services
Services for ASIC Design Houses
KiviCore helps ASIC design houses to navigate the complexity of hardware security with confidence. We offer expert consulting and hardware software co-design services to secure your platform from the ground up, leveraging mechanisms like secure boot, secure firmware update, Hardware Root of Trust (HRoT), and strong cryptographic services.
Outsourcing to KiviCore means
- Expertise on demand
- Predictable cost structures
- No last-minute security blockers before tape-out
Want to learn more about our services? Get in touch.
Why outsourcing instead of doing it in-house?
Security is complex
Cyber security is a highly specialized field with its own tools, standards, and mindset (e.g., threat modeling, side-channel protection, secure boot chains). Trying to handle it internally without proper knowledge can lead to critical security weaknesses.
Cost & resource efficiency
Building an in-house security team is expensive and only pays off if you are running multiple security-heavy projects per year. With KiviCore, you get high-end security expertise exactly when you need it without ongoing headcount costs.
Cutting-Edge Knowledge
Security is constantly evolving, just think about post-quantum cryptography, EU Cyber Resilience Act (CRA), ARM TrustZone architecture updates. KiviCore stays ahead so you don’t have to.
Faster time to market
By outsourcing, you skip the long ramp-up, training, or trial-and-error phases. You get proven methods and drop-in expertise that accelerate your path to secure, certifiable designs.
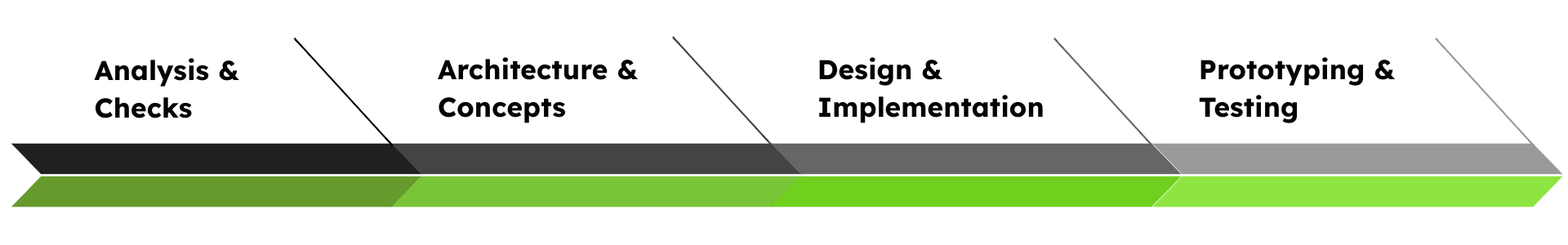
1
Analysis & Check
- Definition of security goals and requirements
- Analysis of existing SoCs & software security concepts and features
- Compliance check & gap analysis of SoCs in relation to cybersecurity standards (e.g. CRA)
- Consulting on PQC and classic cryptographic algorithms
2
Architecture & Concepts
- Development of secure SoC concept & architecture & embedded software
- Optimization of existing SoC security concepts
- Consideration of IP cores & sub systems for secure data transmission, protocol implementations, or key handling e.g. MACsec, IPsec, PQC, ARM Trust Zone
3
Design & Implementation
-
- Analysis and evaluation of different implementation approaches
- Integration of crypto primitive IP cores
- Integration of security mechanisms
- Secure boot
- Secure life cycle
- Secure key exchange
- Secure communication
- Secure updates
- Secure storage
4
Prototyping & Testing
- Development of PoCs for security solutions
- SoC-Design and firmware design
- Carrying out threat analyses and simulation-based security tests
- Verifying security-critical designs to ensure protection against side-channel attacks and other vulnerabilities
Explore our offerings

Cyber Resilience Act
Due to the Cyber Reslience Act manufacturers of microelectronics must take action. Manufacturers must assess which attacks and exploits, regardless of an attacker’s motives, could affect the device.
We offer services to help you with that.

MACSec and Key Agreement
MACsec stands for Media Access Control Security and is a standard to secure point-to-point network communication on the data data link layer (Layer 2) of the OSI 7 layer model.
We offer the development & implementation of MACsec concepts based on MKA and pre-shared keys.

IPSec
IPsec is a Layer 3 encryption technology to secure IP traffic. To utilize this IPsec, an Internet Key Exchange protocol IKEv2 is needed. IKEv2 creates secure associations, negotiates encryption, and generates session keys.
We can help you by creating IPsec and IKE concepts and implementing them onto different target platforms.

ARM SoC Security
ARM processors and SoC architectures are well known and widely used in embedded systems. Implementing security measures to make components and systems more secure is a must have for new products.
We offer services to secure your RISC-V based SoC.

RISC-V SoC Security
RISC-V is an open standard processor architecture, which is used in several applications. Making RISC-V system on chip SoC architectures secure is a must have for new product designs.
We offer services to secure your RISC-V based SoC.