Cyber Resilience Act (CRA)
Cyber Resilience Act Product Check
Not sure if your embedded product is CRA compliant? Find out in just two weeks.
CRA for Embedded Systems
With the Cyber Resilience Act (CRA), the EU creates uniform, binding cyber security requirements for digital products and software for the first time. What looks like regulatory effort at first glance is actually a crucial step towards more trust, quality and competitiveness, especially for innovative companies.
The CRA affects all products with digital elements that are marketed in the EU, from networked devices to software to embedded systems in industrial applications. In the future, companies that develop or sell such products must prove that their products meet basic security requirements. This ranges from secure default settings ("Secure by default") to active weakness management to transparent update processes over the entire product life cycle.
The most important points are:
- Safety aspects must be taken into account in product development and design right from the start ("Security by Design")
- Manufacturers are responsible for conformity throughout the entire product life cycle
- Clear processes are needed to detect, report and remedy security gaps
The challenge:
Smaller companies in particular often do not have their own security teams or experience with regulatory requirements. But if you ignore the CRA, you not only risk fines, but also the market access in the EU. Safety requirements “installed later” is complex, expensive and avoidable.
The chance:
Early compliance shows investors and customers that their company works responsibly, future-proof and marketable. It strengthens trust in its product - especially in security -critical industries such as medical technology, industry or networked infrastructure.
Major steps to achieve conformity
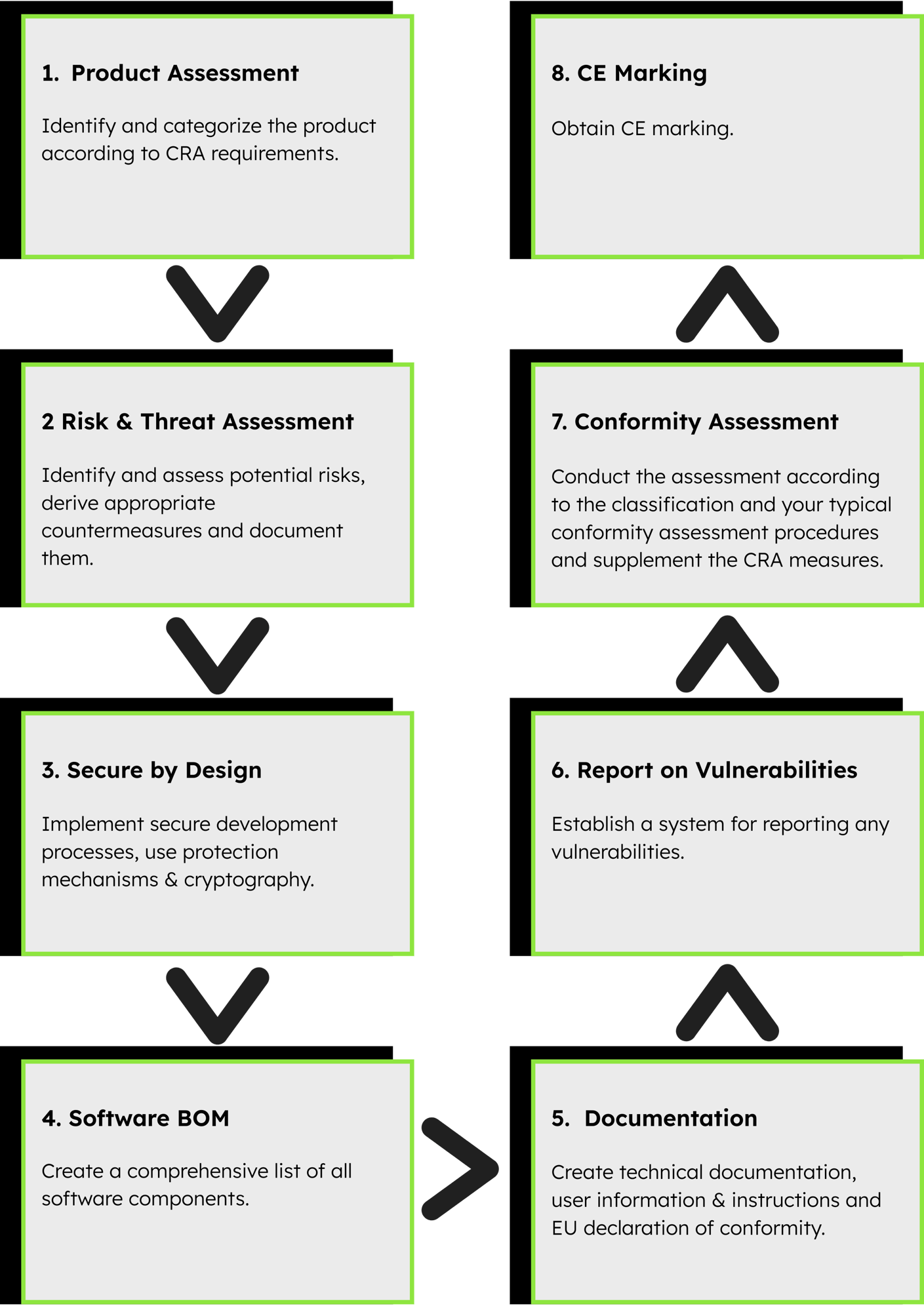
Our Cyber Resilience Act Services
1
Consulting & Analysis
- CRA consulting for embedded products
- Product assessment
- Threat analysis & risk assessment
- Gap analysis
2
Architecture & Concepts
- Definition of security requirements based on analysis and gap analysis
- Development of concepts and architectures
3
Design & Implementation
- Secure development of embedded products
- Hardening of secure embedded systems
- Integration & configuration of security mechanisms
- Secure boot
- Secure life cycle
- Secure key exchange
- Secure communication
- Secure updates
4
Documentation
- Support in preparing SBOM
- Support in preparing documentation for certification
4
Testing
- Development of test concepts
- Testing of security mechanisms and functions
Why KiviCore?
KiviCore´s employees have decades of experience in ASIC and FPGA design and embedded software development. We understand how embedded systems are affected by the Cyber Resilience Act and what technical measures need to be taken to make the product compliant with the CRA. We excel in classic crypto algorithms as well as in cutting-edge cryptographic technologies, including Post-Quantum Cryptography (PQC) and can help you to implement such functionalities into your system.


Our experienced experts and our lean corporate structure enable us to offer our expertise quickly and at a competitive price.

We not only advise you on the impact of the CRA on your product, but also support you with the technical implementation and security architecture that may be required based on the CRA assessment.
Frequently Asked Questions
What are products with digital elements?
Products with digital elements are defined as products that can be connected to a device or a network and include both hardware products with networked functions and pure software products. For embedded developers this means, that both, hardware but also embedded software is affected. Examples of digital products can be software like firmware, end devices like sensors or components like processing units, FPGAs and ASICs.
Are there products which are not affected?
Yes, a few products are excluded from the CRA. The CRA does not apply to products that are already subject to specific cybersecurity requirements under other EU regulations.
These include, among others:
Medical devices (regulated by the Medical Devices Regulation), Vehicles (covered by the type approval regulations), Aviation products & Military products
These exemptions avoid double regulation, as these products already have to meet cybersecurity requirements through their own sectoral regulations.
Who must comply with this regulation?
The CRA applies to all companies that manufacture, import or distribute products with digital elements in the EU.
What is the timeline to comply?
The CRA was adopted by the Council of EU Home Affairs Ministers on October 10, 2024 and will become directly binding law due to its regulation status. Manufacturers and operators have until November 2027 to ensure that their newly introduced products comply with the CRA requirements.
What are the consequences of non-compliance with CRA?
Non-compliance could result in high fines up to 15 million Euros or 2.5% of the annual global turnover, whichever is higher.
